IAM: Users & Groups
So, IAM stands for Identity and Access Management. It is a global service because in IAM we create users and put them into groups.
- IAM means Identity and Access Management.
- IAM is a global service. This means users and groups work in all regions, not just one.
- The root account is made when you create your AWS account. Do not use it for daily work and do not share it.
- Users are people or apps in your organization. You can put users into groups.
- Groups can only have users. They cannot have other groups.
- A user does not need to be in a group, and a user can be in many groups.

IAM: Permissions
- Users or groups can have policies. Policies are JSON documents.
- Policies define what a user can do in AWS.
- AWS uses the least privilege principle: give users only the permissions they need, not more.
Example JSON policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "ec2:Describe*",
"Resource": "*"
},
{
"Effect": "Allow",
"Action": "elasticloadbalancing:Describe*",
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"cloudwatch:ListMetrics",
"cloudwatch:GetMetricStatistics",
"cloudwatch:Describe*"
],
"Resource": "*"
}
]
}
"Version": "2012-10-17"- This is the policy language version. It tells AWS which version of JSON rules we are using."Statement"- This is a list of rules. Each rule says what actions are allowed or denied."Effect": "Allow"- This means the rule allows the action. It could also be"Deny"to block something."Action"- This is what the user can do."ec2:Describe*"- Can see EC2 information (all“Describe”actions)."elasticloadbalancing:Describe*"- Can see load balancer information.- CloudWatch actions - Can list metrics, get statistics, and describe resources.
"Resource": "*"- This means the rule applies to all resources.
In short: This policy gives read-only access to EC2, Load Balancer, and CloudWatch services.
Create Users in AWS
Let’s practice creating users in AWS using the IAM service.
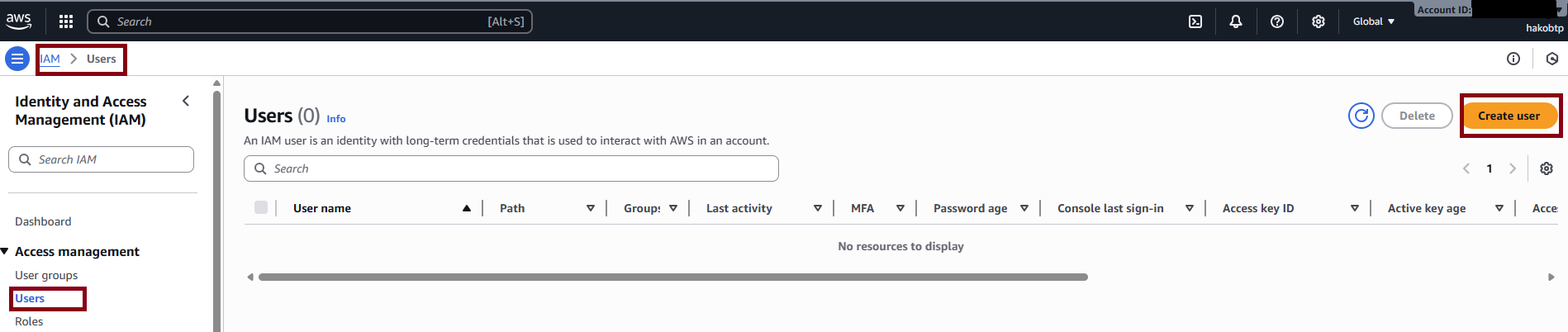
- In the AWS search bar, type IAM and open the IAM console.
- On the IAM Dashboard, you may see some security recommendations. We don’t need to worry about them for now.
- On the left side, click Users. This is where we can create new IAM users.
Important note:
- In the top right corner, click Global. You will see that the region selection is not active.
- This shows that IAM is a global service, not tied to any specific region.
- Users you create in IAM are available everywhere. Some other AWS services you’ll see in this course are region-specific.
Why do we create users?
- Right now, you are using the root account, which shows your account ID.
- Only the AWS account itself has an account ID.
- IAM users do not get a new account ID. They belong to the same AWS account.
- Each IAM user has a username and credentials (like a password or access keys) but shares the account ID with the root account.
- Using the root account for daily work is not safe and not best practice.
- Instead, we create IAM users, such as admin users, so that we can use the account more safely.
Now, let’s go ahead and create a user. On the Users page, click the “Create user” button.
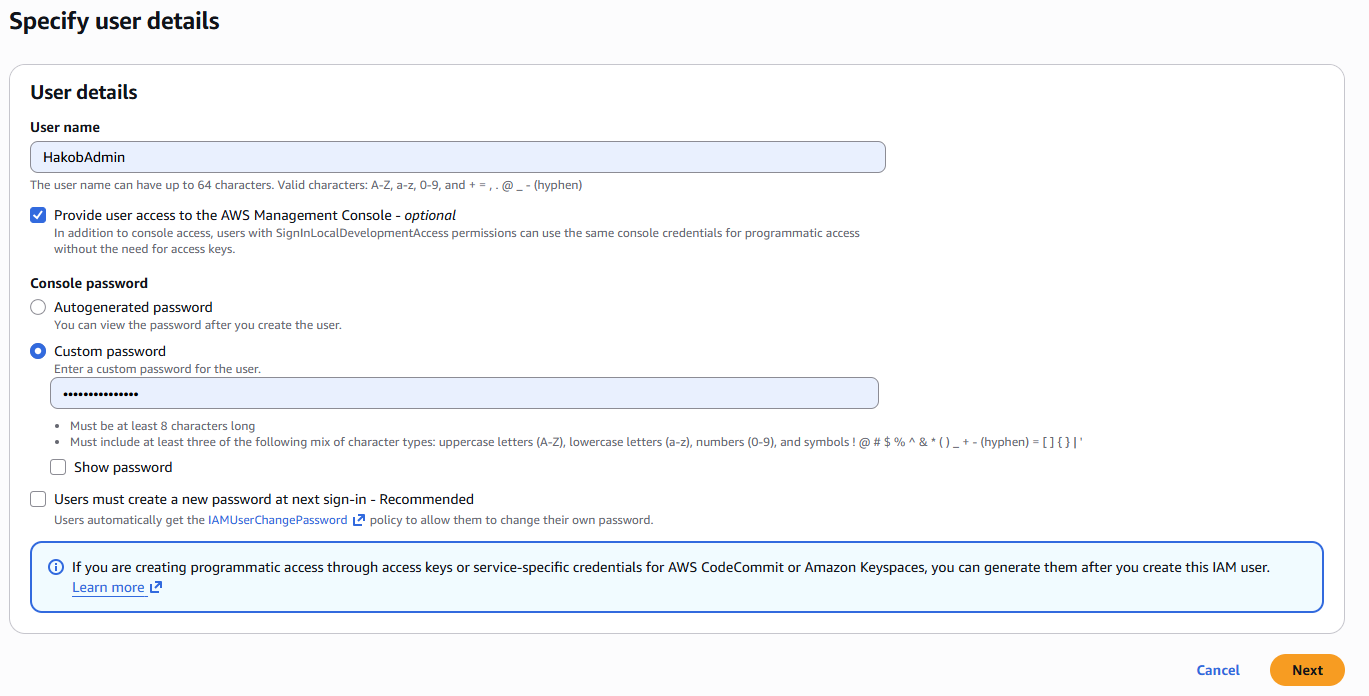
After entering the username, click Next. Now we need to add permissions to the user. You can add permissions directly to the user, or You can use a group to give permissions.
Let’s create a group:
- The group name will be
admin. - The policy for this group will be
AdministratorAccess.
Click the Create group button

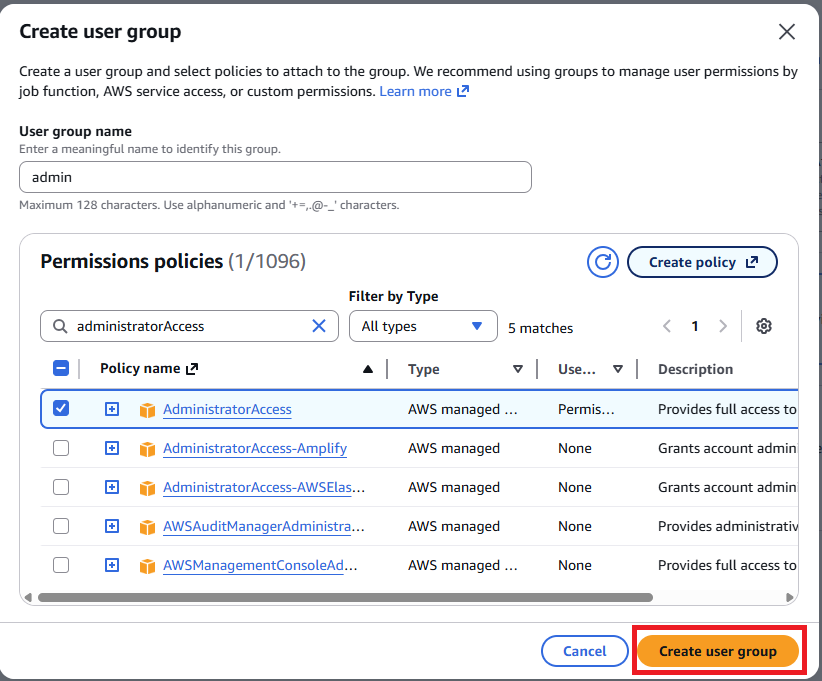
Click Create user group. Now that the group is ready, we can add the user to the admin group.
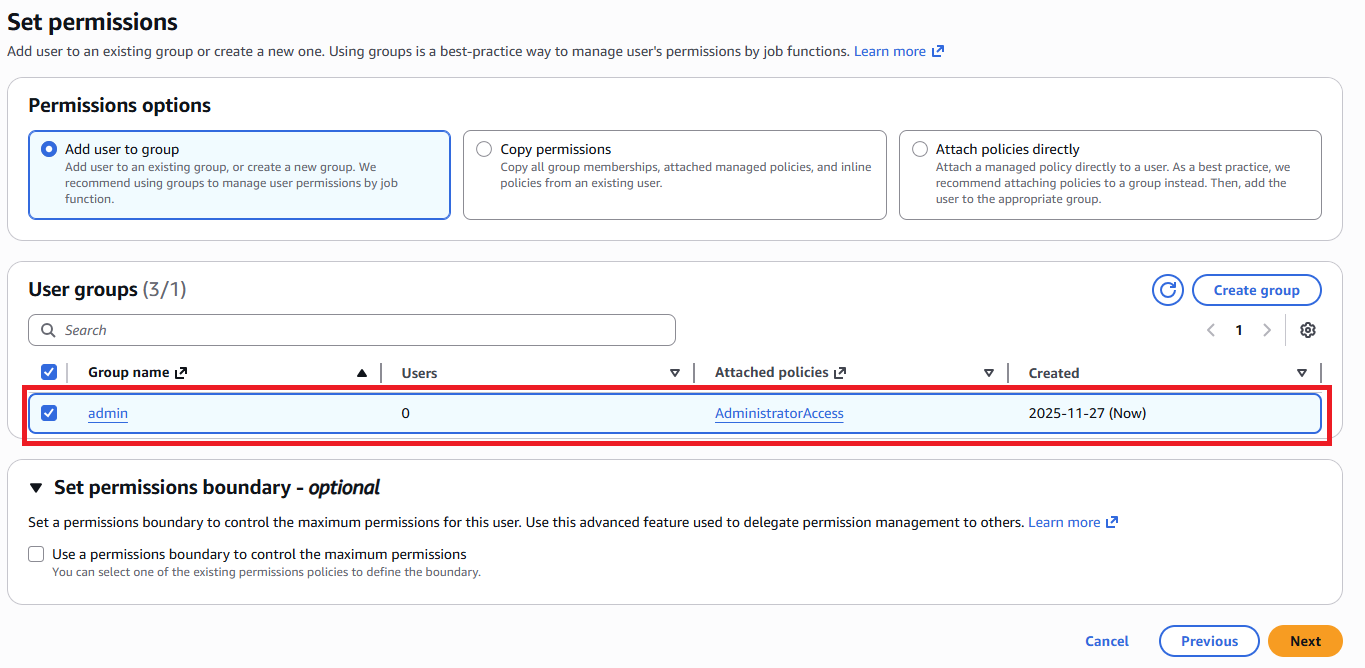
Click Next to go to the Review page.
Here you can check everything before creating the user:
- Username
- Permissions (from the group)
- Tags
- Tags are optional but very useful in AWS.
- They are like labels or metadata for your resources.
- For example, you could add a tag:
- Key: Department
- Value: Engineering
- Tags help you organize and manage resources.
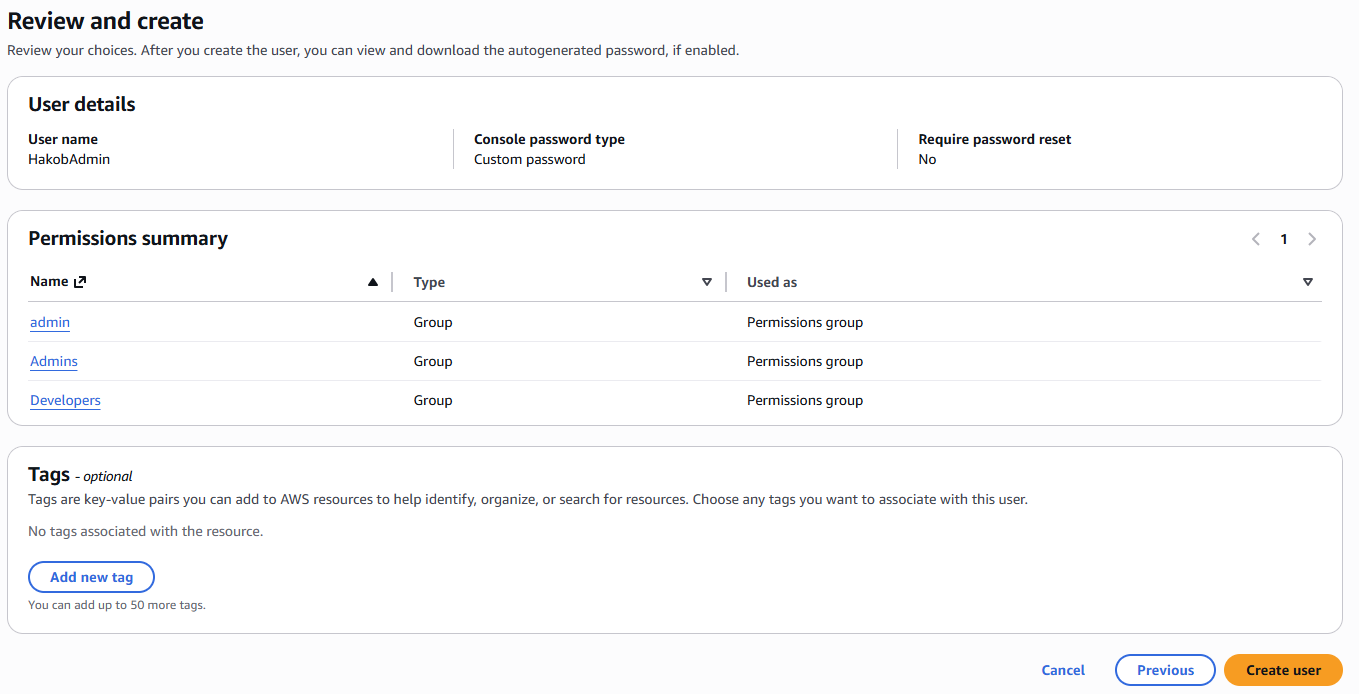
Click Create user. Now the user is created successfully.
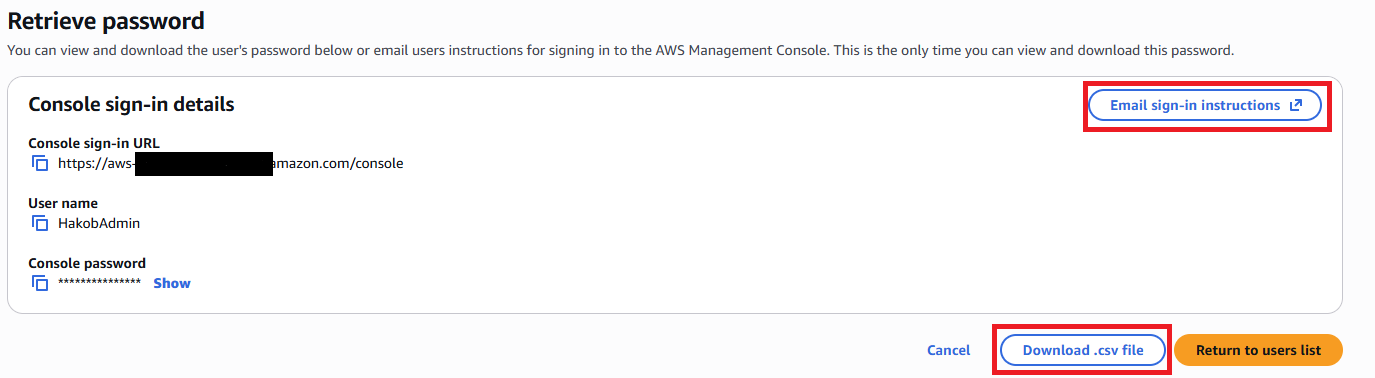
After creating the user, you can:
- Email the sign-in instructions to the user, or
- Download a CSV file with the user’s credentials.
- The user can now log in using their username and password.
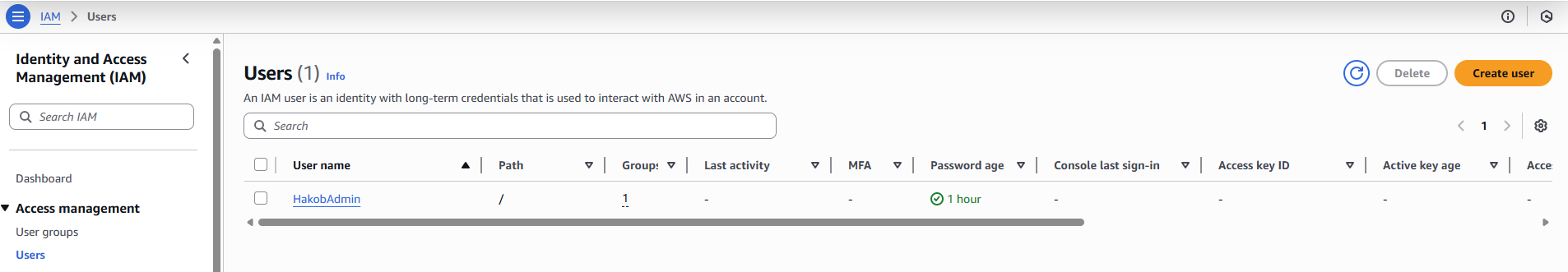
Let’s go back to the user list and check everything. Here we can see user list.
On the left side, if we click User groups, we can see the group called admins.
The admins group has one user in it, named HakobAdmin.
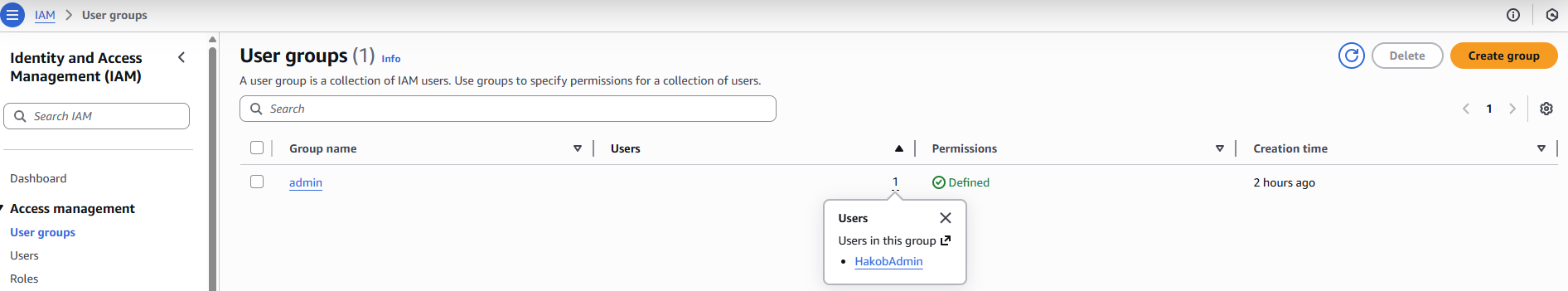
If we look at the permissions of the admins group, we can see that the AdministratorAccess policy is attached to it.

If we open the user HakobAdmin, we can also see the AdministratorAccess policy.
However, this permission was not added directly to the user.
The user received this permission through the admin group.
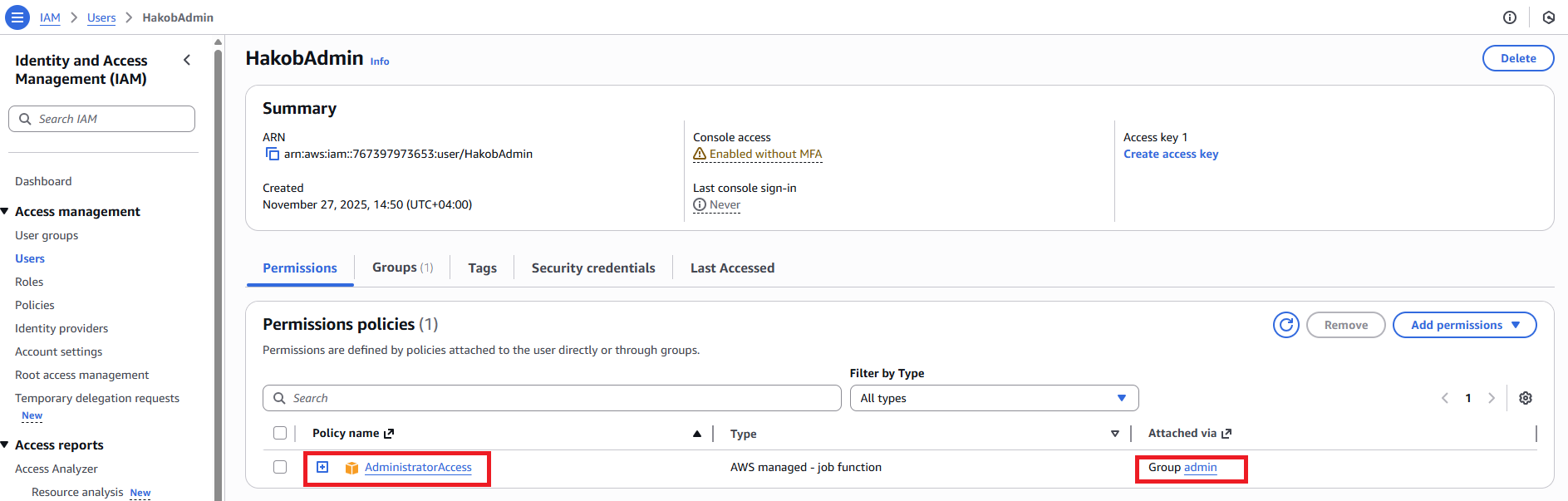
This means that HakobAdmin inherited all the permissions of the group.
This is why we put users in groups—it makes permission management simpler.
Now let’s go back to the IAM Dashboard because we want to sign in with our new user, HakobAdmin.
First, we can look at our AWS account information. The account has an account ID and a sign-in URL.
We can also customize the sign-in URL by creating an account alias.
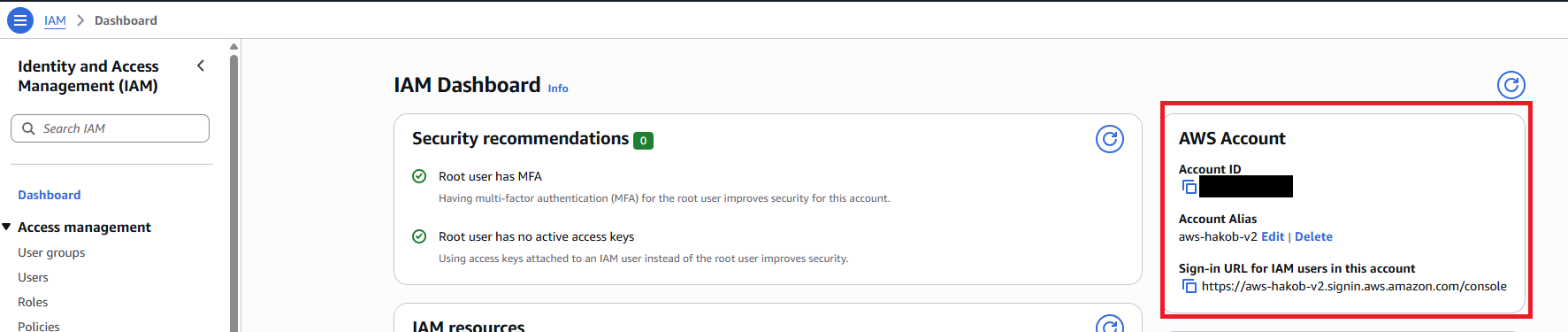
You can Edit or Create alias.
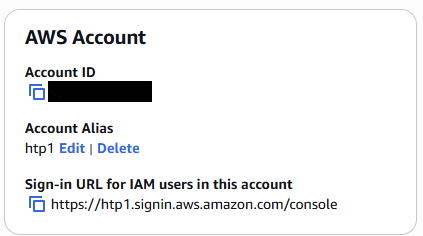
Now you can use https://htp1.signin.aws.amazon.com/console to log in.